- Status
- Offline
- Joined
- Apr 18, 2019
- Messages
- 147
- Reaction score
- 249
Xenos
Windows dll injector. Based on Blackbone library - https://github.com/DarthTon/Blackbone
GitHub
Release

Windows dll injector. Based on Blackbone library - https://github.com/DarthTon/Blackbone
Supports x86 and x64 processes and modules
Kernel-mode injection feature (driver required)
Manual map of kernel drivers (driver required)
Injection of pure managed images without proxy dll
Windows 7 cross-session and cross-desktop injection
Injection into native processes (those having only ntdll loaded)
Calling custom initialization routine after injection
Unlinking module after injection
Injection using thread hijacking
Injection of x64 images into WOW64 process
Image manual mapping
Injection profiles
Kernel-mode injection feature (driver required)
Manual map of kernel drivers (driver required)
Injection of pure managed images without proxy dll
Windows 7 cross-session and cross-desktop injection
Injection into native processes (those having only ntdll loaded)
Calling custom initialization routine after injection
Unlinking module after injection
Injection using thread hijacking
Injection of x64 images into WOW64 process
Image manual mapping
Injection profiles
Relocations, import, delayed import, bound import
Hiding allocated image memory (driver required)
Static TLS and TLS callbacks
Security cookie
Image manifests and SxS
Make module visible to GetModuleHandle, GetProcAddress, etc.
Support for exceptions in private memory under DEP
C++/CLI images are supported (use 'Add loader reference' in this case)
Hiding allocated image memory (driver required)
Static TLS and TLS callbacks
Security cookie
Image manifests and SxS
Make module visible to GetModuleHandle, GetProcAddress, etc.
Support for exceptions in private memory under DEP
C++/CLI images are supported (use 'Add loader reference' in this case)
V2.3.2
- Win10 RS4 update support
V2.3.1
- Win10 Fall Creators update support
- STATUS_UNSUCCESSFUL codes refactored
- Bug fixes
V2.3.0
- Win10 Creators Update support
- Unified injection and manual mapping (injector -> target) : x86->x86, x64->x64, x86->x64, x64->x86
- Bug fixes, stability improvements
V2.2.2
- Bug fixes, stability improvements
V2.2.1
- Win 10 10586 driver compatibility
- Minor GUI usability fixes
- Create process: working dir changed
V2.2.0
- Command line options
- Separate x86/x64 profiles
- Pure IL exe manual mapping
V2.1.4
- VS 2015 runtime
- Win10 RTM support
V2.1.3
- Win10 build 9926 support
- Win8.1 bug fixes
V2.1.2
- Fixed BSOD under win7 and win8.1 systems
- Major kernel manual map bug fixes
- Kernel logs
V2.1.1
- Some logging
V2.1.0
- Kernel manual map for user-mode dlls
- Process handle access rights escalation
V2.0.0
- New GUI
- Injection image list
- Auto-injection
- Injection profiles
- Injection delay timers
- Kernel injection improvements - module unlinking and init routine invocation
- Win10 tech preview support
V1.2.1
- ManuapMap: 'Hide mapped memory region' flag
- Manual map of system drivers
- Self-protection option (Tools -> Protect self)
- Improved injection into suspended process
- 'Close after injection' flag
V1.2.0
- Kernel injection methods
- Various bug fixes
V1.1.2
- Save/load last programm configuration
- Added command line for process launcher
- ManualMap: Discardable sections aren't mapped now (e.g. ".reloc")
V1.1.0
- Added module view
- Module unloading
V1.0.1:
- Fixed bug with remote memory deallocation after manual mapping
- Exception handler aren't created now if process has DEP turned off.
- Win10 RS4 update support
V2.3.1
- Win10 Fall Creators update support
- STATUS_UNSUCCESSFUL codes refactored
- Bug fixes
V2.3.0
- Win10 Creators Update support
- Unified injection and manual mapping (injector -> target) : x86->x86, x64->x64, x86->x64, x64->x86
- Bug fixes, stability improvements
V2.2.2
- Bug fixes, stability improvements
V2.2.1
- Win 10 10586 driver compatibility
- Minor GUI usability fixes
- Create process: working dir changed
V2.2.0
- Command line options
- Separate x86/x64 profiles
- Pure IL exe manual mapping
V2.1.4
- VS 2015 runtime
- Win10 RTM support
V2.1.3
- Win10 build 9926 support
- Win8.1 bug fixes
V2.1.2
- Fixed BSOD under win7 and win8.1 systems
- Major kernel manual map bug fixes
- Kernel logs
V2.1.1
- Some logging
V2.1.0
- Kernel manual map for user-mode dlls
- Process handle access rights escalation
V2.0.0
- New GUI
- Injection image list
- Auto-injection
- Injection profiles
- Injection delay timers
- Kernel injection improvements - module unlinking and init routine invocation
- Win10 tech preview support
V1.2.1
- ManuapMap: 'Hide mapped memory region' flag
- Manual map of system drivers
- Self-protection option (Tools -> Protect self)
- Improved injection into suspended process
- 'Close after injection' flag
V1.2.0
- Kernel injection methods
- Various bug fixes
V1.1.2
- Save/load last programm configuration
- Added command line for process launcher
- ManualMap: Discardable sections aren't mapped now (e.g. ".reloc")
V1.1.0
- Added module view
- Module unloading
V1.0.1:
- Fixed bug with remote memory deallocation after manual mapping
- Exception handler aren't created now if process has DEP turned off.
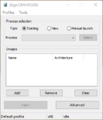
Some option explanations:
Process selection:
Existing - select existing process from the list
New - new process will be launched before injection
Manual launch - after pressing 'Inject' button, injector will wait for target process startup
Images:
List of images you want inject
Add - add new image to the list. Drag'n'drop is also supported
Remove - remove selected image
Clear - clear image list
Advanced options:
Injection type:
Native inject - common approach using LoadLibraryW \ LdrLoadDll in newly created or existing thread
Manual map - manual copying image data into target process memory without creating section object
Kernel(New thread) - kernel mode ZwCreateThreadEx into LdrLoadDll. Uses driver
Kernel(APC) - kernel mode APC into LdrLoadDll. Uses driver
Kernel(Manual map) - kernel manual mapping. Uses driver
Native Loader options:
Unlink module - after injection, unlink module from InLoadOrderModuleList, InMemoryOrderModuleList, InInitializationOrderModuleList, HashLinks and LdrpModuleBaseAddressIndex.
Erase PE - after injection, erase PE headers
Use existing thread - LoadLibrary and init routine will be executed in the context of random non-suspended thread.
Manual map options:
Add loader reference - Insert module record into InMemoryOrderModuleList/LdrpModuleBaseAddressIndex and HashLinks. Used to make module functions (e.g. GetModuleHandle, GetProcAddress) work with manually mapped image.
Manually resolve imports - Image import and delayed import dlls will be also manually mapped instead of being loaded using LdrLoadDll.
Wipe headers - Erase module header information after injection. Also affects manually mapped imports.
Ignore TLS - Don't process image static TLS data and call TLS callbacks.
No exception support - Don't create custom exception handlers that enable out-of-image exception support under DEP.
Conceal memory - Make image memory visible as PAGE_NO_ACESS to memory query functions
Command Line:
Process command line arguments
Init routine:
If you are injecting native (not pure IL) image, this is name of exported function that will be called after injection is done. This export is called as void ( __stdcall* )(wchar_t*) function.
If you are injecting pure managed image, this is name of public method that will be executed using ICLRRuntimeHost::ExecuteInDefaultAppDomain.
Init argument:
String that is passed into init routine
Close after injection:
Close injector after successful injection
Inject delay:
Delay before injection start
Inject interval:
Delay between each image
Escalate handle access:
Bypass handle acess filters. Driver is required
Menu options:
Profiles->Load - load injection profile
Profiles->Save - save current settings into profile
Tools->Eject modules - open module ejection dialog
Tools->Protect self - make injector process protected (driver required)
Command line options:
--load <profile_path> - start injector and load target profile specified by <profile_path>
--run <profile_path> - immediately execute profile specified by <profile_path> without GUI
Kernel injection methods require system running in Test mode.
Process selection:
Existing - select existing process from the list
New - new process will be launched before injection
Manual launch - after pressing 'Inject' button, injector will wait for target process startup
Images:
List of images you want inject
Add - add new image to the list. Drag'n'drop is also supported
Remove - remove selected image
Clear - clear image list
Advanced options:
Injection type:
Native inject - common approach using LoadLibraryW \ LdrLoadDll in newly created or existing thread
Manual map - manual copying image data into target process memory without creating section object
Kernel(New thread) - kernel mode ZwCreateThreadEx into LdrLoadDll. Uses driver
Kernel(APC) - kernel mode APC into LdrLoadDll. Uses driver
Kernel(Manual map) - kernel manual mapping. Uses driver
Native Loader options:
Unlink module - after injection, unlink module from InLoadOrderModuleList, InMemoryOrderModuleList, InInitializationOrderModuleList, HashLinks and LdrpModuleBaseAddressIndex.
Erase PE - after injection, erase PE headers
Use existing thread - LoadLibrary and init routine will be executed in the context of random non-suspended thread.
Manual map options:
Add loader reference - Insert module record into InMemoryOrderModuleList/LdrpModuleBaseAddressIndex and HashLinks. Used to make module functions (e.g. GetModuleHandle, GetProcAddress) work with manually mapped image.
Manually resolve imports - Image import and delayed import dlls will be also manually mapped instead of being loaded using LdrLoadDll.
Wipe headers - Erase module header information after injection. Also affects manually mapped imports.
Ignore TLS - Don't process image static TLS data and call TLS callbacks.
No exception support - Don't create custom exception handlers that enable out-of-image exception support under DEP.
Conceal memory - Make image memory visible as PAGE_NO_ACESS to memory query functions
Command Line:
Process command line arguments
Init routine:
If you are injecting native (not pure IL) image, this is name of exported function that will be called after injection is done. This export is called as void ( __stdcall* )(wchar_t*) function.
If you are injecting pure managed image, this is name of public method that will be executed using ICLRRuntimeHost::ExecuteInDefaultAppDomain.
Init argument:
String that is passed into init routine
Close after injection:
Close injector after successful injection
Inject delay:
Delay before injection start
Inject interval:
Delay between each image
Escalate handle access:
Bypass handle acess filters. Driver is required
Menu options:
Profiles->Load - load injection profile
Profiles->Save - save current settings into profile
Tools->Eject modules - open module ejection dialog
Tools->Protect self - make injector process protected (driver required)
Command line options:
--load <profile_path> - start injector and load target profile specified by <profile_path>
--run <profile_path> - immediately execute profile specified by <profile_path> without GUI
Kernel injection methods require system running in Test mode.
GitHub
Release
Supported OS: Win7 - Win10 x64